Dasha Smolina is an emerging cyber security professional and is currently a Security Engineer in the Eastern U.S. Region at Check Point Software Technologies. She joined Check Point in 2023 to help organizations and businesses meet their cyber security needs.
Overview
The sophisticated cyber threat landscape poses a significant risk to the education sector. Malicious actors’ interest in this sector is growing. Students are often targeted by these attackers because of their increased online presence, risky online behavior, and lack of cyber security awareness. Unlike businesses, which often successfully employ cyber security awareness training to prevent cyber crime incidents, schools overlook cyber security training in their curricula. As young students continue to boundlessly explore the web and are increasingly exposed to cyber threats, K-12 educators need to provide better cyber security training for students to ensure their safety online.
Background – Why are students targeted and what cyber crime are they experiencing?
In the past few years, the internet has become a primary channel for education, with two-thirds of children saying they access their online education resources daily. One in three education devices contains sensitive data, making it critical to keep devices secure.
Students are also more connected to the web than ever before because of the prominence of social media and online gaming. These children are exposed to the internet constantly, relying on it for almost all of their educational and recreational needs. However, they often lack awareness about online safety. As noted previously, attackers are targeting these children because of their increased online presence, risky online behavior, naivety and lack of safety precautions.
K-12 students are experiencing concerning cyber risks such as cyber bullying, inappropriate content, identity theft, and more. Given that 92% of children are online by the age of 12 and that 72% of them having experienced at least one cyber threat, it is evident that students are at risk of attacks by cyber criminals. Moreover, these attacks are multifaceted, with attackers utilizing various techniques to induce harm (see Exhibit 1).
In addition to what was mentioned above, online crimes against children are also high because of the prevalence of children using social media without adult supervision. Nine out of 10 households with internet access have children who are active on social media, and 54% of these households do not regulate their children’s online activities. The lack of supervision and awareness, combined with an increase in online activity means that students are exposed to many cyber security threats.
Exhibit 1 – Boston Consulting Group Survey Results
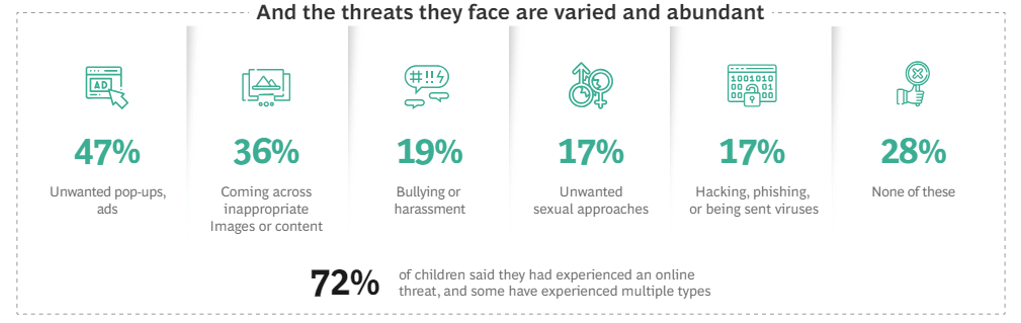
The data shows that one particular cyber threat affects children more commonly than adults: cyber bullying. Cyber bullying is particularly dangerous because it can affect children through all hours of the day and night and can come in many forms such as texting, social media posts, and chatroom messages. Cyber bullying can also be anonymous, which leaves victims with little recourse to report the attacker. Even if the victim knows who the attacker is and blocks or reports them, there are so many avenues through which to hide an identity online that the attacker can easily find another way to harm the victim; it is nearly impossible to escape a determined cyber bully. Cyber bullying has detrimental effects on its victims, leading to mental health issues, increased stress and anxiety, depression, and violence. The effects of cyber bullying have also been shown to be long-lasting, continuing even once the bullying has stopped.
Another long-lasting cyber crime that children are targeted for is identity theft. This dangerous cyber crime ensnares one in 50 children annually and has life-long implications for a child. For those who may not know, identity theft as a cyber crime occurs when an attacker steals a person’s data and information to commit fraudulent identity-based activities, such as opening credit cards or bank accounts, applying for loans, committing online crimes like scams, and more. Children who have had their identity stolen might not find out for years, or even decades, until they try to open their own credit card account and discover that their credit history has been tarnished. Children fall victim to identity theft through data breaches, doxxing (someone else publicly sharing their information or “docs”), parents or close ones oversharing information about the child, children oversharing their information or passwords with friends, and phishing and other common online scams.
Trusting strangers online and naivety can also lead children to become victims of online predators or groomers. Online predators visit popular social media websites and falsify their age and profile content to potentially lure young children into online interactions. Once contact is established, the groomer then pressures the child to reveal explicit photos of themselves and might even try to meet the child in person. Sometimes the groomer will blackmail the child, but other times the victim might not even realize they are being groomed, considering the online predator to be their boyfriend or girlfriend. There are about 500,000 online predators active each day but only two out of ten children are aware of this potential danger. Rather than protecting themselves and limiting potential exposure to dangerous adults online, 40% of children online remove their privacy settings to attract more followers. This makes it that much easier for groomers to access a child’s information and manipulate them online.
Children also fall for online financial scams, as shown by the data collected for the FBI’s 2023 Internet Crime Report, which states that people under the age of 20 accumulated over $40 million worth of losses to online scams in 2023. Online scammers are preying on children who are accessing the internet at early ages and who lack the awareness to recognize cyber threats.
With more children going online at even younger ages, it is no longer as easy as it once was to keep children safe at home. Online threats are infiltrating their lives and putting children in danger of cyber attackers. Given education’s shift towards online learning, students are facing many new kinds of cyber risks. Moreover, with the emergence of new technologies, such as the Internet of Things or cloud-based and network-connect devices, including children’s toys and household appliances, the evolution of threats is not slowing down. Thus, it is important for educators to better understand the situation and help equip students with the knowledge and skills to protect themselves from attackers.
Proposed solution – How can cyber attacks that target students be prevented?
To protect young students from becoming cyber crime victims, educators and parents should increase the cyber security safety measures in-place on children’s devices. They should also provide cyber safety awareness education for children. Oftentimes, once an attack has occurred, the damage is irreparable, and parents can only report the crime and mitigate the impact. Therefore, prevention should be the priority. Combining safety controls with better cyber security education in regards to topics like phishing, privacy, social media safety, and cyber security awareness training will equip students with the tools and skills they need to be safe online.
Since students are provided with devices to access the internet by their parents or their educators, a simple way to better protect students is to employ cyber security solutions on these devices. As education becomes more digital, for school systems that provide tablets and computers for students, Check Point provides a suite of solutions to secure students. These solutions prevent uncontrolled exposure to inappropriate website content, phishing, and advanced cyber threats targeting students and their personal information. Check Point’s cyber security solutions for education protect against all imminent threats, are easy to implement, facilitate meeting compliance mandates, and keep students’ online access safe and regulated. Please reference the Check Point solution overview for K-12 education here: https://www.checkpoint.com/downloads/products/harmony-education-solution-brief.pdf
For parents providing devices for their children, Check Point offers a similar consumer product, ZoneAlarm, which incorporates features from the Check Point Harmony suite to prevent malware, phishing, ransomware, and other zero-day threats. Please reference the Zone Alarm information here: https://www.zonealarm.com/
For over 30 years, Check Point’s mission has been to secure the digital world for everyone, everywhere and we pursue this mission by preventing attacks before they happen with an industry-leading 99.8% threat prevention rate. So, the best way to secure the devices that young children are using is to install prevention-first cyber security solutions onto the devices.
While securing the devices helps prevent attacks from happening, a multi-layered approach to security should also include cyber security awareness education programs. Safe internet use lessons for children, including topics like keeping information private on social media, being wary of online scammers, and how to report/stop cyber bullying, would greatly benefit students. Based on a report from the Children’s Commissioner, parents share an average of 71 photos and 29 videos of their children every year and children will share their own content to social media over 70,000 times by age 18. This abundance of information makes it easy for attackers to profile their victims and use the information that they post against them.
Educating parents and children about limiting the personal information that they share online will help prevent attacks. Educating students about different types of scams and attacks will also help prevent children from engaging in cyber bullying and with online financial scammers. Teaching kids to be critical thinkers and practicing situational awareness when engaging with cyber space will better ensure that they are on-guard and don’t fall prey to basic scams that cause tremendous harm.
If this cyber security education is provided to students in a way that is engaging and easy to understand, students will regain the knowledge effectively. Creating lesson plans that contain interesting topics, like generative AI, social media safety, and preventing online gaming scams, will ensure a fun learning experience and an abundance of engagement on the part of the students. Bringing in guest cyber security speakers or employing online games are great ways for educators to teach cyber security topics without requiring the educators to be cyber security experts themselves. There is an abundance of options for helping students be safe online and it is extremely important that students are equipped with the tools and skills to remain safe in the increasingly dangerous online environment.
K-12 cyber security education resources
Fun online games (all games have NO LOGIN requirements to ensure students do not have to share any information to engage with the content)
- https://sos.fbi.gov
- Game for 3rd – 8th graders that works on tablets, mobile devices, or computers. Covers topics including internet safety, online etiquette, smart sharing, securing systems, and protecting against attackers.
- https://beinternetawesome.withgoogle.com/en_us
- Game for 2nd – 6th graders that works on tablets, mobile devices, or computers. Game is available in multiple languages. Covers topics including smart sharing, recognizing scams, staying secure online, online etiquette, and how to report online incidents.
- https://www.pbs.org/wgbh/nova/labs/lab/cyber/
- Game for 4th – 8th grade students that works on computers. The game is designed to teach students how to recognize and thwart cyber attacks. Students play as a startup company with in-sufficient security and are tasked with creating a security strategy to prevent hackers from infiltrating their company.
- https://overthewire.org/wargames/
- Game for 8th – 12th grade students that works on computers. This game is more advanced and tasks students with learning cyber security topics while practicing ssh and linux scripting skills.
- https://public.cyber.mil/training/cyber-awareness-challenge/
- Training style game for 7th – 12th graders that works on computers. This game is geared towards teaching users how to mitigate threats and vulnerabilities. The training provides an overview of cyber threats and best practices to stay secure online.
#000, #2023, #Accounts, #Ai, #Anxiety, #Approach, #Attackers, #Awareness, #Background, #Behavior, #Challenge, #Channel, #CheckPoint, #CheckPointSoftware, #Children, #Cloud, #Compliance, #Computers, #Consulting, #Content, #CreditCard, #Crime, #Cyber, #CyberAttackers, #CyberAttacks, #CyberCrime, #CyberCriminals, #CyberSecurity, #CyberSecurityAwareness, #CyberSecurityEducation, #CyberSecurityTraining, #CyberThreat, #CyberThreats, #Data, #DataBreaches, #Depression, #Devices, #Easy, #Education, #Effects, #Engineer, #Environment, #Evolution, #Experienced, #FBI, #Features, #Financial, #Forms, #Game, #Games, #Gaming, #Generative, #GenerativeAi, #Hackers, #Health, #History, #Household, #How, #HowTo, #Identity, #IdentityTheft, #Impact, #Industry, #Internet, #InternetOfThings, #Issues, #It, #K12, #K12Education, #Kids, #Landscape, #Languages, #Learning, #Life, #Limiting, #Linux, #Loans, #Lure, #Malware, #Media, #MentalHealth, #Mitigate, #Mobile, #MobileDevices, #Network, #One, #OnlineGames, #OnlineLearning, #OnlineSafety, #OPINION, #Organizations, #Other, #Passwords, #Pdf, #Phishing, #Photos, #Play, #Predators, #Prevent, #Prevention, #PreventionFirst, #Privacy, #Profile, #PublicSector, #Ransomware, #Report, #Reports, #Resources, #Risk, #Risks, #Safety, #Scams, #School, #Scripting, #Securing, #Security, #SecurityAwareness, #SecurityEngineer, #SecurityTraining, #Sensitive, #SituationalAwareness, #Skills, #Social, #SocialMedia, #Software, #Space, #Ssh, #Startup, #Strategy, #Stress, #Students, #SurveyResults, #Teachers, #Teaching, #ThreatLandscape, #ThreatPrevention, #Threats, #ThreatsAndVulnerabilities, #Tools, #Toys, #Training, #TRENDINGNOW, #Victims, #Videos, #Vulnerabilities, #Web, #Websites, #ZeroDayThreats, #ZoneAlarm
Published on The Digital Insider at https://is.gd/uAXpPK.
Comments
Post a Comment
Comments are moderated.